Hardware Hacking Lab: Analysis Tools
Hardware Hacking Lab Series Overview
Are you wondering how to get started with embedded device security testing and what tools are needed for hardware hacking? Whether you are trying to reverse engineer and hack an embedded system or are looking to make modifications to an IoT device, our Hardware Hacking Lab series will introduce you to some of the tools we rely upon to perform our smart device security assessments.
This is the second post in this series. Please check out part one on Physical Tools if you haven’t already done so!
Analysis Tools Overview
This post will focus on the hardware analysis tools that we use in our assessments. We’re going to break this down into a few different categories:
Note: we have no relationship with any of these companies or products - we simply have found them useful and are passing on our experiences with these tools to you. Have other suggestions? Please leave a comment below with your recommendations!
Electrical & Signal Analysis

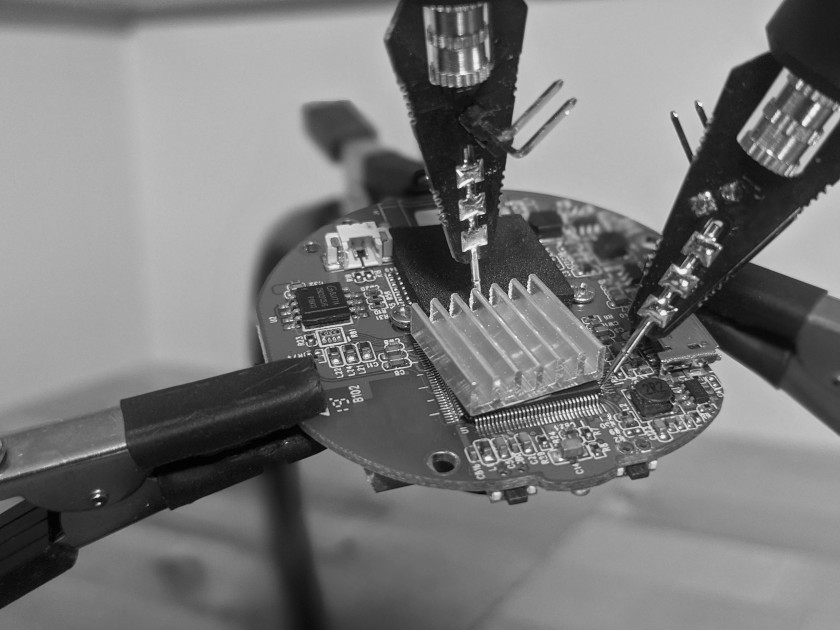
Let’s start with the basics here. Before we can hook up a debugger or programmer to interact with the device or extract memory, we need to understand the hardware and its capabilities. While looking up the device in the FCC registry and reading chip datasheets are extremely valuable activities, it’s often useful to map out pins to exposed debug ports using a multimeter. You can make this more manageable with a good set of leads or these excellent probe tips.
Sometimes it isn’t easy to access the chip pins without damaging the device, so we like to get a feel for what type of electrical signals are passing through a pin or pad using an oscilloscope. You can verify your understanding of what functions certain components expose with specialized tools or logic analyzers. If you can’t afford much, I’d suggest getting a logic analyzer before an oscilloscope.
Potential shopping list
Again, we have no association with the vendors linked below so shop around and support your local shops when possible! Prices listed are what we paid when we bought these, so your experience may be different.
- Extech EX330 Multimeter ( $51)
- Bionso 25-Piece Multimeter Leads Kit ( $23)
- Tag-Connect Probe Covers ( $30)
- Rigol DS1054Z Oscilloscope ( $349)
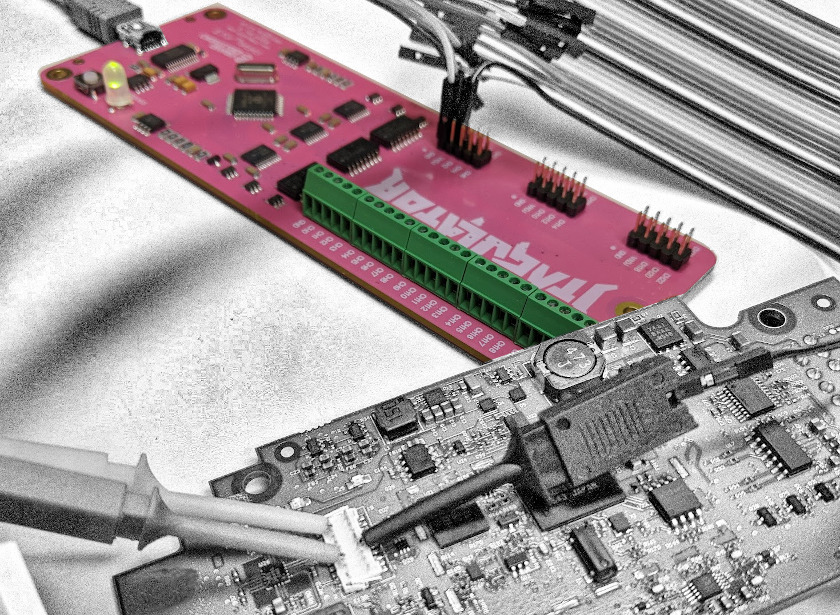
- JTAGulator ( $179
- Logic Analyzers
Debuggers & Programmers

Once you’ve verified where the serial, communications, and programming connections are, it’s time to break out the debuggers and programmers. Many of the tools below have similar uses, so you certainly don’t need to buy everything on this list. We’d suggest starting with one or two multi-purpose tools to interface with embedded protocols like JTAG, I2C, SPI, and UART. We also like using dedicated tools to communicate with UART or JTAG/SWD/SWO. When those tools don’t suffice, we tend to buy development kits for specific chipsets so we can use the same tools our clients’ developers use (e.g. STM8/32, EFR32, etc). Sometimes we find removing a chip and using a dedicated flash reader/programmer to be the most effective.
Potential shopping list
Again, we have no association with the vendors linked below so shop around and support your local shops when possible! Prices listed are what we paid when we bought these, so your experience may be different.
- Multi-purpose Tools
- Vendor-specific Tools
- Serial Tools
- TL866ii Plus Programmer ( $129)
RF Communication

In addition to ripping apart a device to see what it does, it’s also essential to intercept, modify, and repeat the signals sent and received by the device. When it comes to interacting with Bluetooth services and characteristics, you can get by with a cheap adapter or, even better, a dongle made by Nordic. To effectively capture Bluetooth communication, you’ll need something a bit more powerful that can hop frequencies and act as a capture device in Wireshark. There are also specialized devices that can capture, repeat, and transmit Bluetooth packets.
There are many options for capturing, repeating, and transmitting generic RF communications, from cheap rx-only dongles to powerful rx/tx tools. It’s also essential to get some sutiable antennas and adapters if needed.
You’ll also want some way to intercept network communication. We test devices through one of our attack dropboxes since they can perform machine-in-the-middle attacks via their two network interface cards or by acting as a Wi-Fi hotspot using a USB dongle. If the device has a cellular modem and SIM slot, it’s worth seeing if you can get on the same cellular network as the device using a USB modem as well. Some device, especially medical devices, might use infrared for programming or communication so you might want to pick up an IR transmitter/receiver.
Potential shopping list
Again, we have no association with the vendors linked below so shop around and support your local shops when possible! Prices listed are what we paid when we bought these, so your experience may be different.
- Bluetooth
- RF
- Wi-Fi
- WiFi USB Dongle ( $13)
- Cellular
- Hologram Nova ( $55
- Infrared
- MagicW IR Transmitter & Receiver ( $8)
Automotive / CAN

Many of the specialized industrial/commercial IoT projects we perform have some type of automotive component (forklifts, vehicle in-dash control units, etc). Since we usually work on test benches and not complete mechanical systems, having some tools available to sniff the CAN bus can help detect if an attack against the IoT component can result in a message on the bus. There are often other components plugged into the OBD-II port, so it’s helpful to have a Y splitter and adapters to convert between OBD-II and DB9 (unless your sniffer already uses the OBD-II connector, but we prefer using DB9 tools with converters).
Potential shopping list
Again, we have no association with the vendors linked below so shop around and support your local shops when possible! Prices listed are what we paid when we bought these, so your experience may be different.
What’s Next?
You now have the right physical and analysis tools to hack most devices. Feel free to reach out to us if you need additional help getting started with embedded device security!
Let us know what you think
Please share this post if you found it useful and reach out if you have any feedback or questions!
Big Breaks Come From Small Fractures.
You might not know how at-risk your security posture is until somebody breaks in . . . and the consequences of a break in could be big. Don't let small fractures in your security protocols lead to a breach. We'll act like a hacker and confirm where you're most vulnerable. As your adversarial allies, we'll work with you to proactively protect your assets. Schedule a consultation with our Principal Security Consultant to discuss your project goals today.