What To Expect During A Threat Modeling Session With Fracture Labs
A threat modeling session is a collaborative brainstorming exercise with you and your team. An effective session will help ensure you and your security partners are on the same page and may uncover potential attacks you never would have considered!
-
Identify the Crown Jewels
We begin the process by sitting down with your team. We listen to you describe your organization and your project and ask questions to get to the root of what it is you’d like to protect — your crown jewels.
-
Identify the Risks
Once we've identified your crown jewels, we work with you to map out what could go wrong in protecting these assets. We take an honest look at the impact a breach could have on the confidentiality, integrity and availability of these assets to your business.
-
Identify the Threat Vectors
Now that we know what's important to you and what could go wrong, we turn to what our security consultants do best: we think like hackers and plan how we would actually attack your products or systems. We don't think in terms of the intended use of your products or systems — we think about how we could exploit them to help us get to the crown jewels.
This process can be very enlightening and will help you decide which level of security engineering and testing is appropriate for your project. The final deliverable is a mind map showing you exactly where we think you’re most at risk. We use this to help guide our testers during security assessments and penetration tests and map any issues we find back to the threat model. This allows your organization to prioritize which weaknesses to address first.
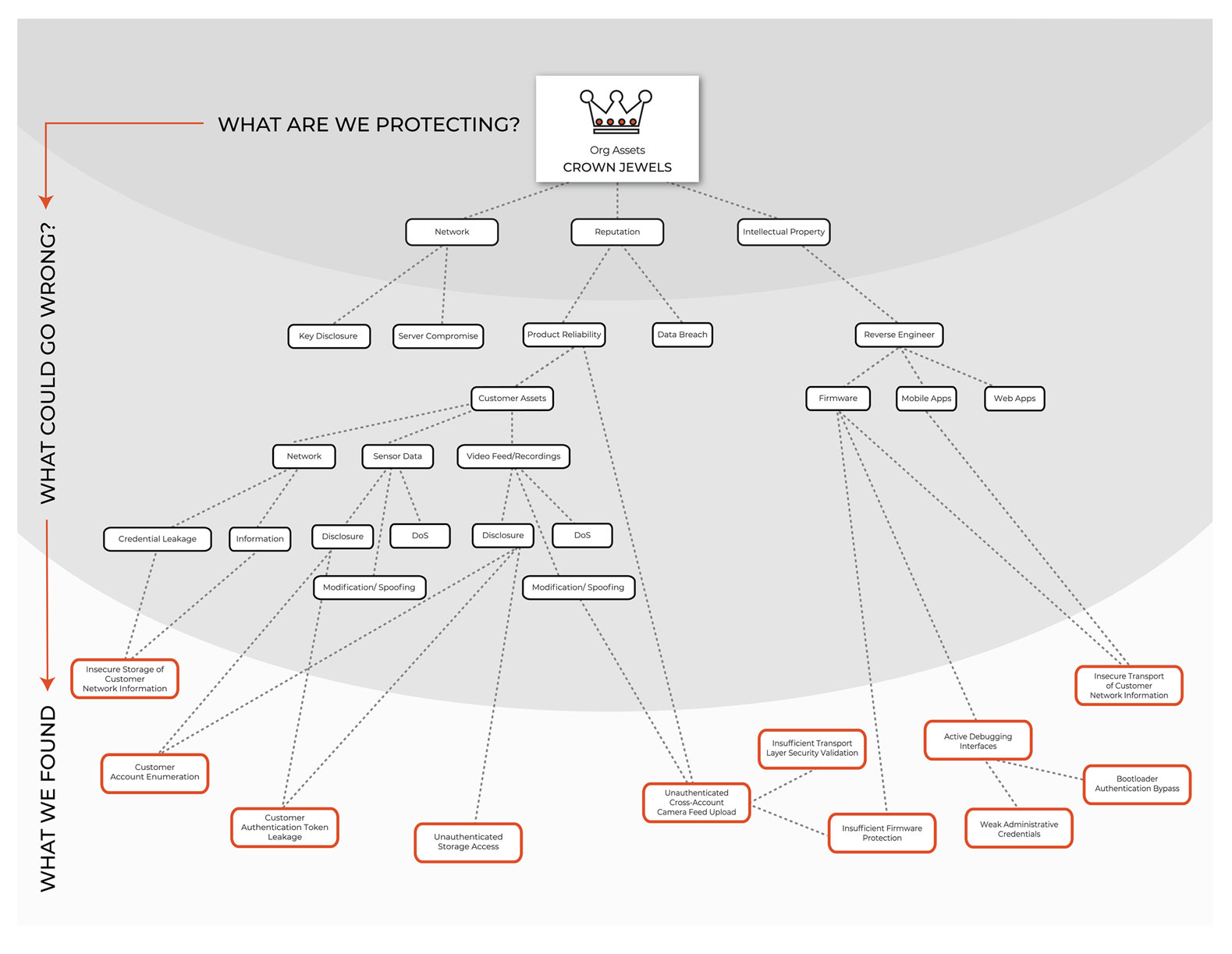
Example threat model deliverable from Fracture Labs
Threat Modeling Success Stories
Weaknesses in Aircraft Network
We identified attack vectors and weaknesses in the proposed design for an aircraft network that otherwise would have made it to the final implementation. This was before any testing activities.
Decreased Security Assessment Budget by 76%
We cut the effort and budget for a proposed web application security assessment by 76% through an extensive pre-testing threat modeling session focused on potential attack vectors. The testing still revealed severe issues for which we had previously predicted, but limited funds were able to be moved from testing to remediation with budget to spare!
From the blog
Check out our blog to get the latest infosec how-to articles, best practices and strategies written by our offensive security experts. Cyber crime isn't going anywhere, so stay informed and on top of it!
DEEP608 Conference - IoT: The 'S' Stands for Security
Fracture Labs presents at DEEP608 regarding the risks IoT devices pose to organizations and what can be done to reduce the risk.
RF Replay Attacks: Hacking Christmas Tree Lights
Fracture Labs uses Christmas tree lights as an example of how easy it is to hack poorly implemented RF communication found in many IoT devices.
Effective Spring4Shell Scanning and Safe Exploitation
Scanning for and exploiting the Spring4Shell vulnerability can be tricky, but this post will show you how to scan more effectively using custom tools from Fracture Labs
Big Breaks Come From Small Fractures.
You might not know how at-risk your security posture is until somebody breaks in . . . and the consequences of a break in could be big. Don't let small fractures in your security protocols lead to a breach. We'll act like a hacker and confirm where you're most vulnerable. As your adversarial allies, we'll work with you to proactively protect your assets. Schedule a consultation with our Principal Security Consultant to discuss your project goals today.