-
Exploiting MS17-010 on Windows Embedded 7 Devices
The Windows SMB remote code execution vulnerability patched by MS17-010 has resulted in widespread attacks against Windows 7 devices. While much of the focus has been on patching desktops and servers, many organizations to continue to neglect devices running the Windows Embedded 7 OS because a public exploit hasn’t existed - until now. Check out how we patched the NSA’s Fuzzbunch tool to demonstrate the importance of patching all devices in a timely manner.
-
Threat Intel RSS Feeds via Twitter Lists
Many security researchers take time to publish their scripts, tips, successes, and failures on Twitter for all to see. As a security professional, it’s important to learn how to effectively use Twitter so you don’t miss anything, but how do you manage to sift through everything? Check out this post on how to turn your Twitter Lists into manageable RSS feeds so you can stay on top of what’s important to you!
-
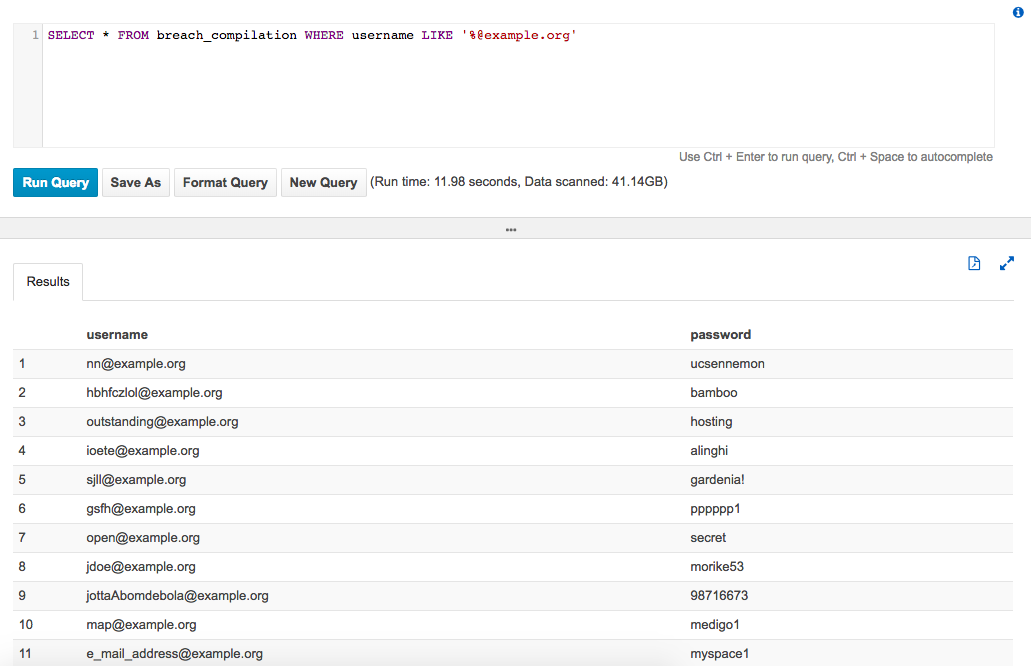
Search Breach Data Quicker with AWS Athena
Most password breach files are organized by user account, but it can be beneficial to search by domain name instead. That can take far too long for massive breach files, so check out this post that shows you how to harness the power of AWS Athena to quickly find the data you need for your next penetration test!
Big Breaks Come From Small Fractures.
You might not know how at-risk your security posture is until somebody breaks in . . . and the consequences of a break in could be big. Don't let small fractures in your security protocols lead to a breach. We'll act like a hacker and confirm where you're most vulnerable. As your adversarial allies, we'll work with you to proactively protect your assets. Schedule a consultation with our Principal Security Consultant to discuss your project goals today.