-
IoT Security Sessions - ESC San Jose 2021
Joe Hopper shares his expertise in IoT security at the 2021 Embedded Sytems Conference in San Jose. ‘Live Hack: Exposing Common IoT Security Weaknesses’ and ‘Internet of Insecure Things: Through the Eyes of a Hacker.’
-
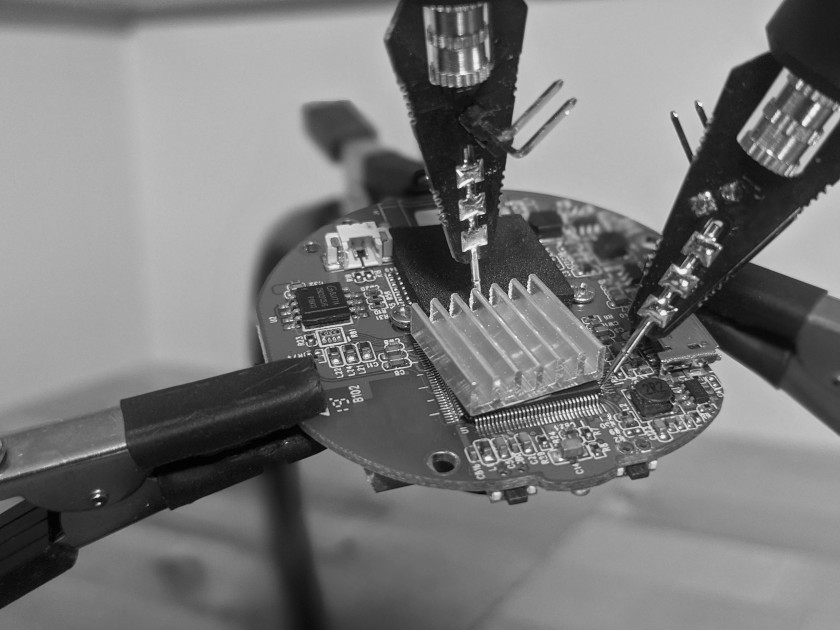
Hardware Hacking Lab: Analysis Tools
Check out part two in our Hardware Hacking Lab series, where we show you what you need in order to build your own lab. We walk you through the analysis tools we use to perform our smart device penetration testing.
-
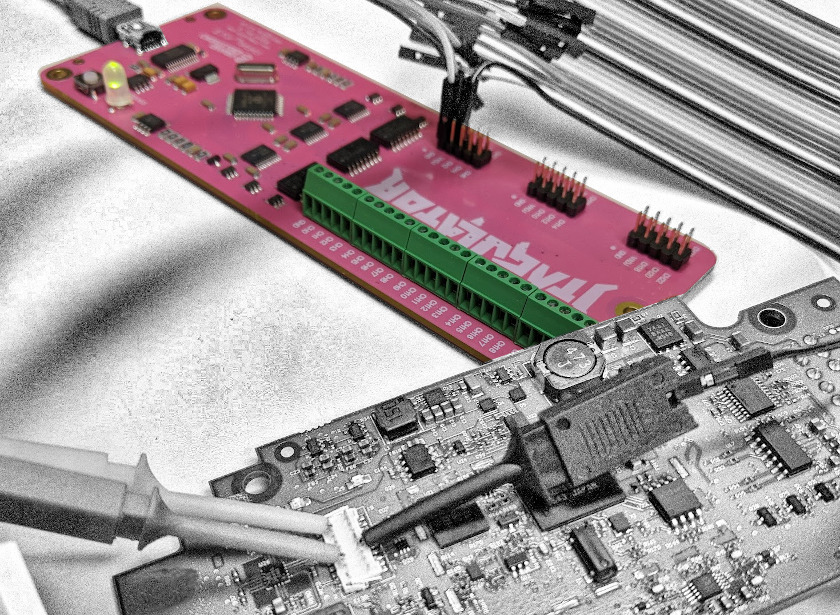
Hardware Hacking Lab: Physical Tools
We’ve kicked off a Hardware Hacking Lab series, where we show you what you need in order to build your own lab. In part one, you’ll learn what physical tools we use to perform our smart device penetration testing.
Big Breaks Come From Small Fractures.
You might not know how at-risk your security posture is until somebody breaks in . . . and the consequences of a break in could be big. Don't let small fractures in your security protocols lead to a breach. We'll act like a hacker and confirm where you're most vulnerable. As your adversarial allies, we'll work with you to proactively protect your assets. Schedule a consultation with our Principal Security Consultant to discuss your project goals today.